Binary Backups of your Mikrotik
Summary
Easily manage and automate Mikrotik binary backups with MKController for fast recovery, cloning, and rollback in critical network scenarios.
Effective network management fundamentally depends on the ability to quickly recover configurations in case of hardware failures, configuration errors, or other unforeseen events. In the Mikrotik RouterOS ecosystem, one of the most powerful tools to ensure this resilience is the binary backup. Unlike an export backup (which generates a text script with commands), the binary backup creates a complete and faithful copy of the router’s configuration in a binary format.
Use Cases and Best Practices
Binary backups are ideal for:
- Disaster Recovery: Quickly restore the complete configuration after a hardware failure.
- Configuration Cloning: Replicate a router’s configuration to another identical device (although it’s crucial to note that MAC addresses are also copied, which may require attention in some network topologies).
- Rollback: Revert to a known stable configuration after an unsuccessful change.
The MKController platform simplifies and automates this process, ensuring that binary backups are performed regularly and stored securely, as we will see next.
Managing Binary Backups in MKController: Step-by-Step
First, authenticate to your MKController account via the address: https://app.mkcontroller.com.
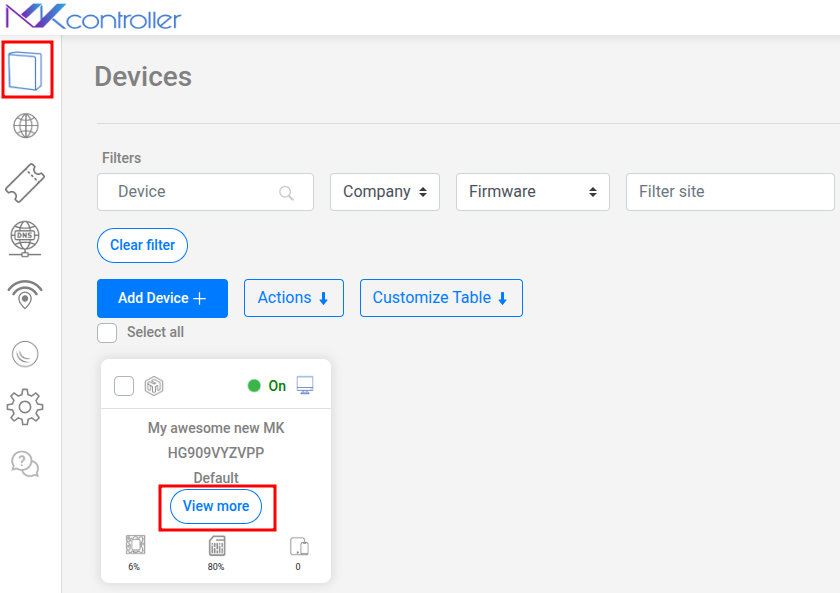
In the main dashboard, locate the “Devices” menu.
Identify the specific Mikrotik router for which you want to manage backups. Click the “View more” button associated with that device to access its detailed options.
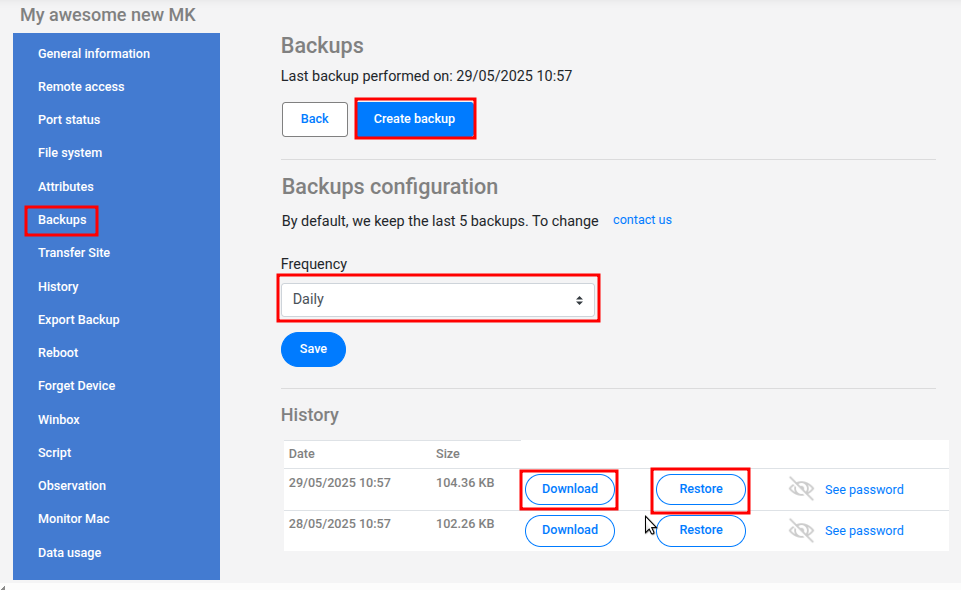
Within the device options, find and select the “Backups” section. This area centralizes all functionalities related to binary backups.
It’s important to note that, by default, MKController already performs binary backups (.backup) of your Mikrotik automatically every day. The platform stores the last 5 automatic backups, ensuring you always have a recent history of configurations.
Although automatic backups are convenient, there might be situations where you want to create a one-time backup, for example, before making a significant configuration change. To do this, simply click the “Create backup” button. The platform will initiate the process of generating a new binary file at that moment.
In the backup list, you will see both automatically generated and manual files. For each listed backup, the following options will be available:
- Download: Allows you to download the
.backupfile for local storage or analysis. Remember to store these files in a secure location, following security best practices. - Restore: Initiates the process of restoring the Mikrotik configuration using the selected backup file. Use this option cautiously, aware that it will overwrite the device’s current configuration and that, ideally, the restoration should be done on the same RouterOS version the backup was created on.
This simplified process offered by MKController ensures that the critical task of maintaining updated backups is performed consistently and accessibly.
Conclusion: Ensuring Network Continuity and Security
Implementing a solid backup routine is an essential pillar for the responsible administration of any network, and Mikrotik RouterOS devices offer robust tools for this purpose through binary backups. As we’ve seen, this method allows for a faithful and complete copy of the equipment’s configuration, enabling quick and effective restorations in case of failures or the need for reversion.
Adopting the practice of regular binary backups, combined with the facilities of MKController, is not just a preventive measure but a strategic investment in the resilience and continuity of your business. It ensures that, in the face of unforeseen events, your network can be re-established with minimal impact, protecting your operations and user trust. Therefore, explore MKController’s backup features and ensure your Mikrotik configurations are always protected.
